Black Hat USA 2016 — конференция, собирающая вместе лучшие умы в области безопасности (хакеров и ЦРУшников), чтобы определить, в каком будущем мы будем жить. Что было в Вегасе, то остается в Вегасе. Но все же до нас дошли видеозаписи 120 докладов.

Я немного подсуетился и выбрал личный список топ-18 самых интересных докладов, которые, возможно, стоит перевести на русский и опубликовать на Хабре.
Социальная инженерия, DDoS, лингвистические особенности телефонных мошенников, страхование в области ИБ, Dragons&Dungeons для кибербезопасности, атаки по сторонним каналам, много (черного) юмора, дроны.
Предлагайте свои варианты, какой доклад самый интересный, может я что-то упустил.
Список от DARKreading 10 Hottest Talks at Black Hat USA 2016
- Advanced CAN Injection Techniques for Vehicle Networks
- Breaking FIDO: Are Exploits In There?
- Design Approaches for Security Automation
- Timing Attacks Have Never Been So Practical: Advanced Cross-Site Search Attacks
- Windows 10 Mitigation Improvements
- The Linux Kernel Hidden Inside Windows 10
- 1000 Ways to Die in Mobile OAuth
- GATTacking Bluetooth Smart Devices—Introducing a New BLE Proxy Tool
- Into The Core—An In-Depth Exploration of the Windows 10 IoT Core
- A Lightbulb Worm?
How to Make People Click on a Dangerous Link Despite Their Security Awareness
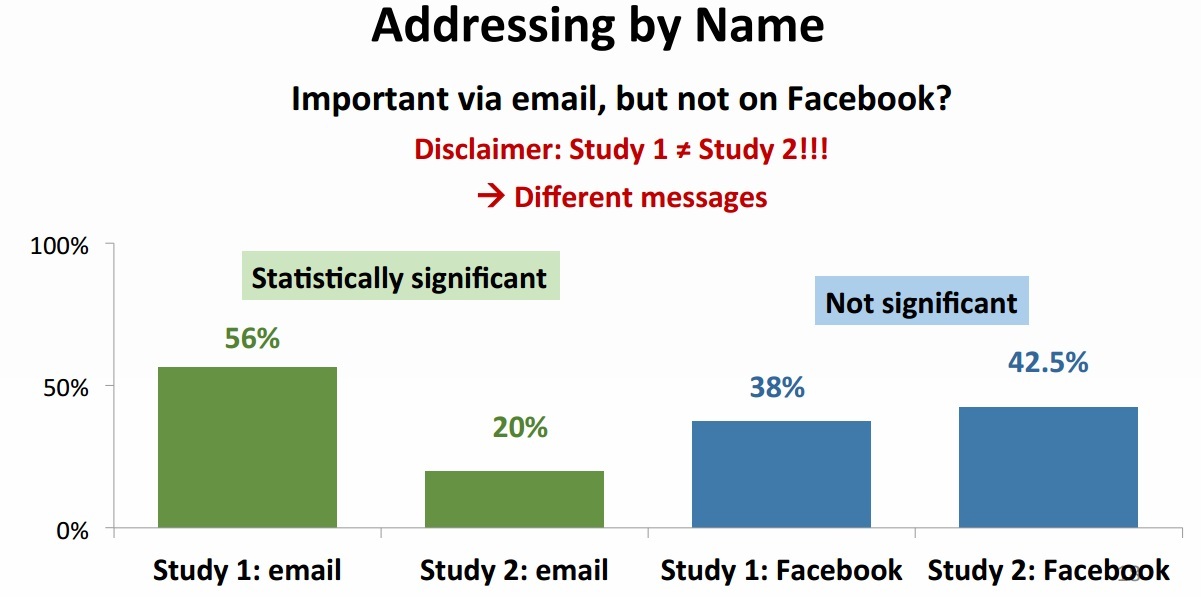
Call Me: Gathering Threat Intelligence on Telephony Scams to Detect Fraud
Drone Attacks on Industrial Wireless: A New Front in Cyber Security

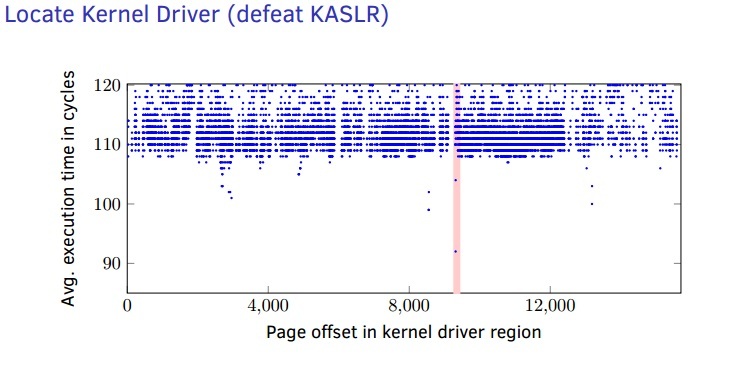
Using Undocumented CPU Behavior to See Into Kernel Mode and Break Kaslr in the Process
Secure Penetration Testing Operations: Demonstrated Weaknesses in Learning Material and Tools
1000 Ways to Die in Mobile Oauth
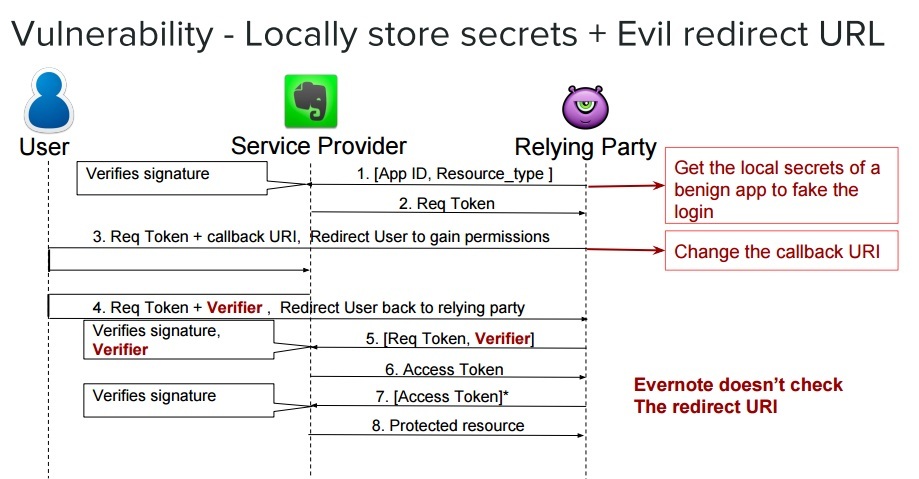
An Insider's Guide to Cyber-Insurance and Security Guarantees

Investigating DDOS — Architecture Actors and Attribution
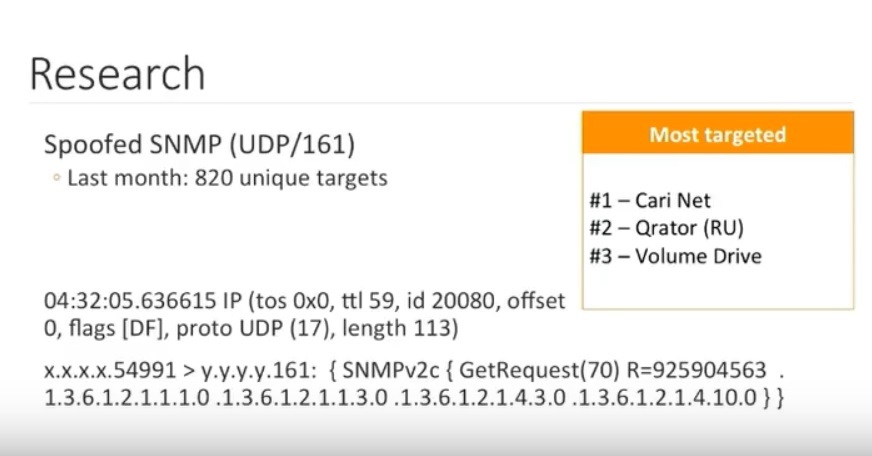
Language Properties of Phone Scammers: Cyberdefense At the Level of the Human

The Tao of Hardware the Te of Implants
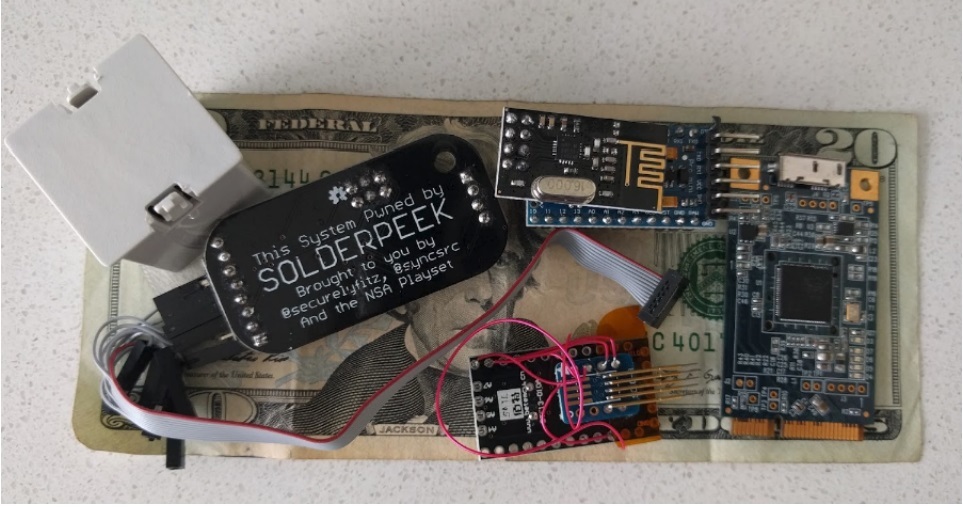
Weaponizing Data Science for Social Engineering: Automated E2E Spear Phishing on Twitter
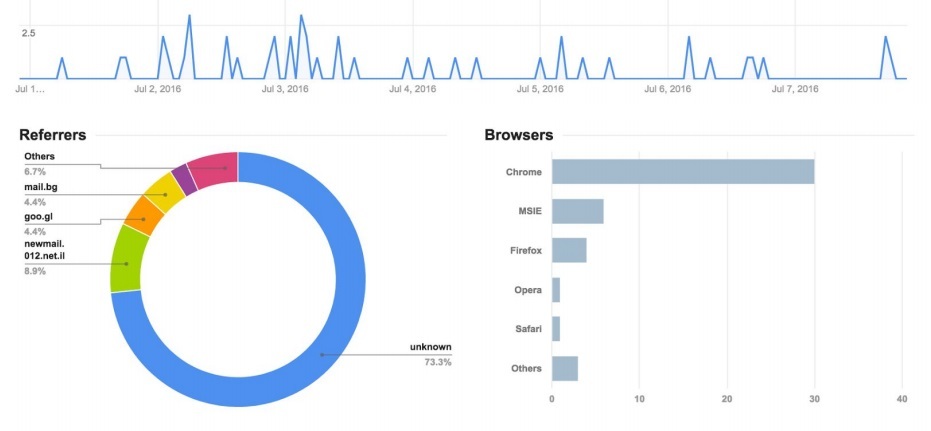
Cyber War in Perspective: Analysis From the Crisis in Ukraine
Security Through Design — Making Security Better By Designing for People

Side-Channel Attacks on Everyday Applications
Dungeons Dragons and Security
VoIP Wars: the Phreakers Awaken

Defense At Hyperscale: Technologies and Policies for a Defensible Cyberspace
Brute-Forcing Lockdown Harddrive Pin Codes
Список всех докладов
Плейлист тут: Black Hat USA 2016 PlayList
- Why This Internet Worked How We Could Lose It and the Role Hackers Play
- A Journey From JNDI/LDAP Manipulation to Remote Code Execution Dream Land
- The Art of Defense — How Vulnerabilities Help Shape Security Features and Mitigations in Android
- Call Me: Gathering Threat Intelligence on Telephony Scams to Detect Fraud
- Applied Machine Learning for Data Exfil and Other Fun Topics
- Canspy: A Platform for Auditing Can Devices
- Dangerous Hare: Hanging Attribute References Hazards Due to Vendor Customization
- Over the Edge: Silently Owning Windows 10's Secure Browser
- How to Make People Click on a Dangerous Link Despite Their Security Awareness
- Certificate Bypass: Hiding and Executing Malware From a Digitally Signed Executable
- Pay No Attention to That Hacker Behind the Curtain: A Look Inside the Black Hat Network
- Drone Attacks on Industrial Wireless: A New Front in Cyber Security
- Hackproofing Oracle Ebusiness Suite
- Using Undocumented CPU Behavior to See Into Kernel Mode and Break Kaslr in the Process
- Gattacking Bluetooth Smart Devices — Introducing a New BLE Proxy Tool
- Measuring Adversary Costs to Exploit Commercial Software
- Removing Roadblocks to Diversity
- HEIST: HTTP Encrypted Information Can Be Stolen Through TCP-Windows
- Memory Forensics Using Virtual Machine Introspection for Cloud Computing
- Secure Penetration Testing Operations: Demonstrated Weaknesses in Learning Material and Tools
- Nonce-Disrespecting Adversaries: Practical Forgery Attacks on GCM in TLS
- Towards a Holistic Approach in Building Intelligence to Fight Crimeware
- Subverting Apple Graphics: Practical Approaches to Remotely Gaining Root
- The Remote Malicious Butler Did It!
- Xenpwn: Breaking Paravirtualized Devices
- PWNIE
- An Open Collaborative Effort to Ameliorate Android N-Day Root Exploits
- Understanding HL7 2.X Standards, Pen Testing, and Defending HL7 2.X Messages
- 1000 Ways to Die in Mobile Oauth
- A Retrospective on the Use of Export Cryptography
- Windows 10 Segment Heap Internals
- Abusing Bleeding Edge Web Standards for Appsec Glory
- AMSI: How Windows 10 Plans to Stop Script-Based Attacks and How Well It Does It
- Analysis of the Attack Surface of Windows 10 Virtualization-Based Security
- Augmenting Static Analysis Using Pintool: Ablation
- An Insider's Guide to Cyber-Insurance and Security Guarantees
- Cunning With Cng: Soliciting Secrets From Schannel
- Beyond the Mcse: Active Directory for the Security Professional
- Does Dropping Usb Drives in Parking Lots and Other Places Really Work?
- Demystifying the Secure Enclave Processor
- I Came to Drop Bombs: Auditing the Compression Algorithm Weapon Cache
- Breaking Payment Points of Interaction (POI)
- Into the Core: In-Depth Exploration of Windows 10 IoT Core
- Hacking Next-Gen Atms: From Capture to Cashout
- Can You Trust Me Now? An Exploration Into the Mobile Threat Landscape
- Investigating DDOS — Architecture Actors and Attribution
- Intra-Process Memory Protection for Applications on ARM and X86: Leveraging the ELF ABI
- Capturing 0Day Exploits With Perfectly Placed Hardware Traps
- Next-Generation of Exploit Kit Detection By Building Simulated Obfuscators
- HTTP/2 & Quic — Teaching Good Protocols to Do Bad Things
- Pwning Your Java Messaging With Deserialization Vulnerabilities
- Language Properties of Phone Scammers: Cyberdefense At the Level of the Human
- Recover a RSA Private Key From a TLS Session With Perfect Forward Secrecy
- The Linux Kernel Hidden Inside Windows 10
- O-Checker: Detection of Malicious Documents Through Deviation From File Format Specifications
- The Tao of Hardware the Te of Implants
- Access Keys Will Kill You Before You Kill the Password
- Hell on Earth: From Browser to System Compromise
- Discovering and Exploiting Novel Security Vulnerabilities in Apple Zeroconf
- BadWPAD
- Breaking Kernel Address Space Layout Randomization (Kaslr) With Intel TSX
- Airbnbeware: Short Term Rentals Long Term Pwnage
- Account Jumping Post Infection Persistency & Lateral Movement in AWS
- Captain Hook: Pirating Avs to Bypass Exploit Mitigations
- Hardening AWS Environments and Automating Incident Response for AWS Compromises
- Crippling HTTPs With Unholy PAC
- Horse Pill: A New Type of Linux Rootkit
- Design Approaches for Security Automation
- Greatfet: Making Goodfet Great Again
- SGX Secure Enclaves in Practice: Security and Crypto Review
- Using EMET to Disable EMET
- Weaponizing Data Science for Social Engineering: Automated E2E Spear Phishing on Twitter
- Viral Video — Exploiting Ssrf in Video Converters
- AVLeak: Fingerprinting Antivirus Emulators for Advanced Malware Evasion
- Windows 10 Mitigation Improvements
- Brute-Forcing Lockdown Harddrive Pin Codes
- Building a Product Security Incident Response Team: Learnings From the Hivemind
- Bad for Enterprise: Attacking BYOD Enterprise Mobile Security Solutions
- Cyber War in Perspective: Analysis From the Crisis in Ukraine
- Breaking Fido: Are Exploits in There?
- Security Through Design — Making Security Better By Designing for People
- Iran's Soft-War for Internet Dominance
- Side-Channel Attacks on Everyday Applications
- The Risk From Power Lines: How to Sniff the G3 and Prime Data and Detect the Interfere Attack
- Unleash the Infection Monkey: A Modern Alternative to Pen-Tests
- OSS Security Maturity: Time to Put on Your Big Boy Pants!
- Watching Commodity Malware Get Sold to a Targeted Actor
- PanGu 9 Internals
- A Lightbulb Worm?
- BadTunnel: How Do I Get Big Brother Power?
- PLC-Blaster: A Worm Living Solely in the PLC
- A Risk-Based Approach for Defining User Training and Awarding Administrative Privileges
- Dungeons Dragons and Security
- The Year in Flash
- Dark Side of the DNS Force
- VoIP Wars: the Phreakers Awaken
- Keystone Engine: Next Generation Assembler Framework
- Pindemonium: A DBI-Based Generic Unpacker for Windows Executable
- Web Application Firewalls: Analysis of Detection Logic
- Defense At Hyperscale: Technologies and Policies for a Defensible Cyberspace
- Crumbling the Supercookie and Other Ways the Fcc Protects Your Internet Traffic
- Advanced Can Injection Techniques for Vehicle Networks
- What's the DFIRence for ICS?
- Samsung Pay: Tokenized Numbers Flaws and Issues
- Breaking Hardware-Enforced Security With Hypervisors
- Behind the Scenes of iOS Security
- HTTP Cookie Hijacking in the Wild: Security and Privacy Implications
- Ouroboros: Tearing Xen Hypervisor With the Snake
- Dptrace: Dual Purpose Trace for Exploitability Analysis of Program Crashes
- TCP Injection Attacks in the Wild — a Large Scale Study
- The Art of Reverse Engineering Flash Exploits
- Timing Attacks Have Never Been So Practical: Advanced Cross-Site Search Attacks
- Using An Expanded Cyber Kill Chain Model to Increase Attack Resiliency
- When Governments Attack: State Sponsored Malware Attacks Against Activists Lawyers and Journalists
- An Ai Approach to Malware Similarity Analysis: Mapping the Malware Genome With a Deep Neural Network
- User Attitudes Toward Security and Usability Tradeoffs for Key-Directory Encryption Systems
- Attacking SDN Infrastructure: Are We Ready for the Next-Gen Networking?
- Building Trust & Enabling Innovation for Voice Enabled IoT
- The Beast Within — Evading Dynamic Malware Analysis Using Microsoft.com
- Handling Technical Assistance Demands From Law Enforcement
Статьи «по мотивам» выступлений на русском
Вы нашли флешку. Стоит ли ее использовать?
Does Dropping Usb Drives in Parking Lots and Other Places Really Work?
слайды
Исследователь нашел бреши в платежной системе Samsung Pay, но Samsung все отрицает
Samsung Pay: Tokenized Numbers, Flaws and Issues
слайды
Поддержка публикации — компания Edison, которая разрабатывает приложение для проектирования быстровозводимых домов, а так же пишет софт для диспетчеризации большегрузного транспорта на угольном разрезе.
Автор: Edison





