First of all let's remember a standart group policy precedence: Local — Site — Domain — Organisation Unit (LSDOU). From less specific level to more specific. It means that Local GPO settings will apply first, then Site-level, Domain-level etc. And the last applied (OU GPO) settings have the highest precedence on the resulting system. However, if a domain administrator didn't set some settings in the higher-level GPOs (e.g. Enable/Disable Windows Defender service) but the same settings have been configured on the Local-level GPO — the last ones will be apply. Yes, even the machine is a domain member.
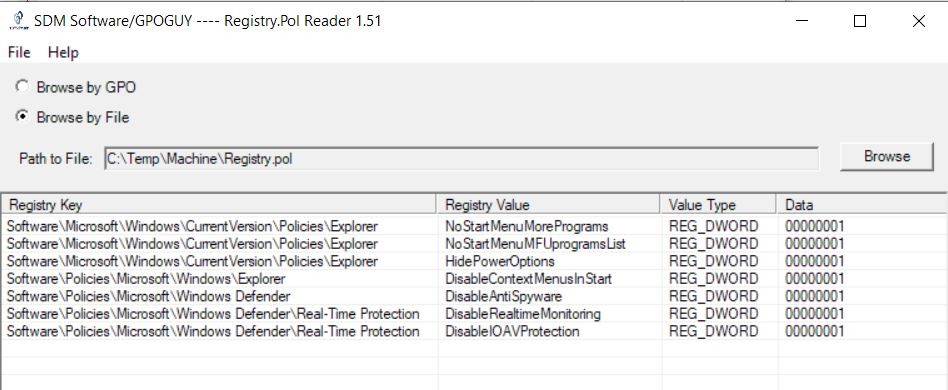
The Local GPO files are located in %systemroot%System32GroupPolicy hidden folder and, of course, it has two scopes (located in subfolders): for User and for Computer. Any user (here I mean a «bad guy» of course), having access to this folder(s), can copy a Registry.pol file and check/change a Local GPO settings. An intruder can use a third-part apllication, such as a RegPol Viewer: